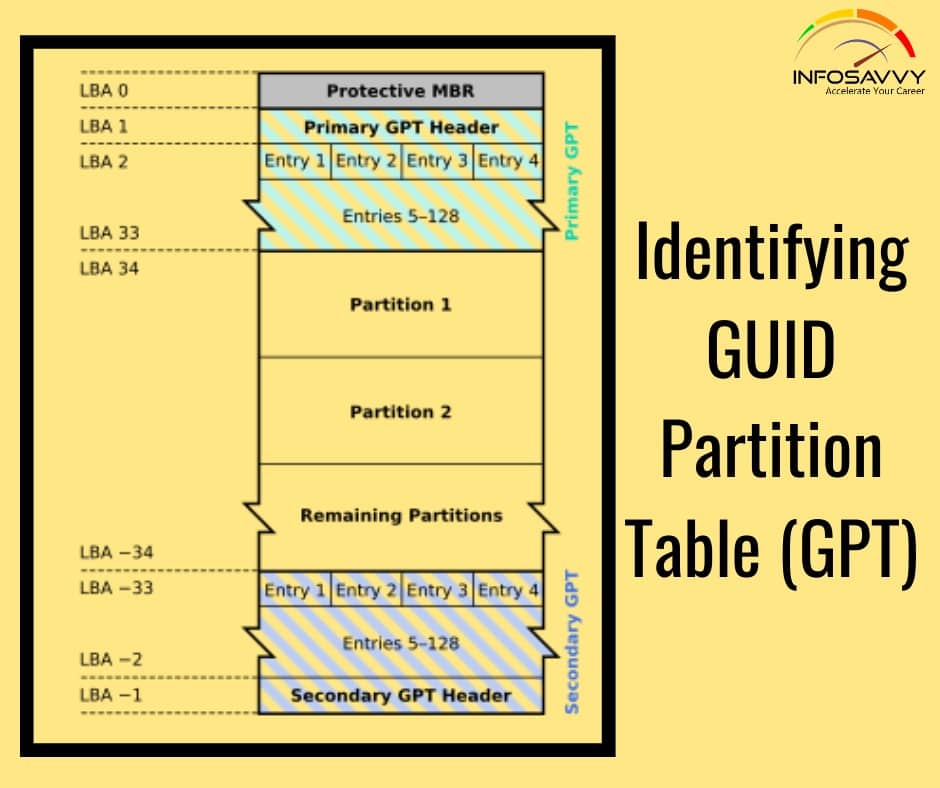
Identifying GUID Partition Table (GPT)
Identifying GUID Partition Table (GPT) in this GPT header will help an investigator analyze the layout of the disk including the locations of the partition table, partition area, and backup copies of the header and partition table. Investigators can use cmdlets given below in Windows PowerShell to identify the presence of GPT: Get-GPT Get-GPT command helps investigator to analyze the GUID Partition Table data structure of the hard disk. It requires the use of the …