Learn about IPv4 Routing Protocols in this the routing (forwarding) process depends heavily on having an accurate and up-to-date IP routing table on each router. This section takes another check out routing protocols, considering the goals of a routing protocol, the methods routing protocols use to teach and learn routes, and an example.
First, consider the goals of a routing protocol, no matter how the routing protocol works:
- To dynamically learn and fill the routing table with a route to every subnet within the internetwork.
- If more than one route to a subnet is available, to place the best route within the routing table.
- To note when routes within the table are not any longer valid, and to remove them from the routing table.
- If a route is removed from the routing table and another route through another neighboring router is available, to add the route to the routing table. (Many people view this goal and therefore the preceding one as one goal.)
- To work quickly when adding new routes or replacing lost routes. (The time between losing the route and finding a working replacement route is called convergence time.)
- to stop routing loops.
Routing protocols all use some similar ideas to permit routers to find out routing information from one another . Of course, each routing protocol works differently; otherwise, you’d not need more than one routing protocol.
Also Read : Introduction to Popular TCP/IP Applications
However, many routing protocols use the same general steps for learning routes:
Step 1. Each router, independent of the routing protocol, adds a route to its routing table for every subnet directly connected to the router.
Step 2. Each router’s routing protocol tells its neighbors about the routes in its routing table, including the directly connected routes and routes learned from other routers.
Step 3. After learning a new route from a neighbor, the router’s routing protocol adds a route to its IP routing table, with the next-hop router of that route typically being the neighbor from which the route was learned. for instance , Figure 4-12 shows the same sample network as in Figure 4-11, but now with attention on how the three routers each learned about subnet 150.150.4.0. Note that routing protocols do more work than is implied within the figure; this figure just focuses on how the routers study subnet 150.150.4.0.
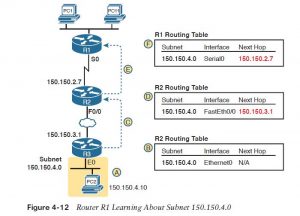
Follow items A through F shown within the figure to see how each router learns its route to 150.150.4.0. All references to Steps 1, 2, and three ask the list just before Figure 4-12.
Step A. Subnet 150.150.4.0 exists as a subnet at the bottom of the figure, connected to Router R3.
Step B. R3 adds a connected route for 150.150.4.0 to its IP routing table (Step 1); this happens without help from the routing protocol.
Step C. R3 sends a routing protocol message, called a routing update, to R2, causing R2 to find out about subnet 150.150.4.0 (Step 2).
Step D. R2 adds a route for subnet 150.150.4.0 to its routing table (Step 3).
Step E. R2 sends an identical routing update to R1, causing R1 to find out about subnet 150.150.4.0 (Step 2).
Step F. R1 adds a route for subnet 150.150.4.0 to its routing table (Step 3). The route lists R1’s own Serial0 because the outgoing interface and R2 because the next-hop router IP address (150.150.2.7).
Chapter 19, “Learning IPv4 Routes with RIPv2,” covers routing protocols in additional detail. Next, the final major section of this chapter introduces several additional functions related to how the network layer forwards packets from source to destination through an internetwork.
Other Network Layer Features
The TCP/IP network layer defines many functions beyond the function defined by the IPv4 protocol. Sure, IPv4 plays a huge role in networking today, defining IP addressing and IP routing. However, other protocols and standards, defined in other Requests For Comments (RFC), play an important role for network layer functions also . for instance , routing protocols like Open Shortest Path First (OSPF) exist as separate protocols, defined in separate RFCs.
This last short section of the chapter introduces three other network layer features that should be helpful to you when reading through the rest of this book. These last three topics just help fill during a few holes, helping to offer you some perspective, and helping you create sense of later discussions also . The three topics are
- Domain name System (DNS)
- Address Resolution Protocol (ARP)
- Ping
Using Names and therefore the domain name System
Can you imagine a world during which whenever you used an application, you had to think about the other computer and ask it by IP address? rather than using easy names like google.com or facebook.com, you’d need to remember and sort IP addresses, like 74.125.225.5. Certainly, that might not be user friendly and will drive some people faraway from using computers in the least . Thankfully, TCP/IP defines how to use hostnames to spot other computers. The user either never thinks about the other computer or refers to the other computer by name.
Then, protocols dynamically discover all the required information to permit communications supported that name. for instance , once you open an internet browser and sort within the hostname www.google.com, your computer doesn’t send an IP packet with destination IP address www.google.com; it sends an IP packet to an IP address used by the online server for Google. TCP/IP needs how to let a computer find the IP address used by the listed hostname, which method uses the name System (DNS).
Enterprises use the DNS process to resolve names into the matching IP address, as shown within the example in Figure 4-13. during this case, PC11, on the left, must connect to a server named Server1. At some point, the user either types within the name Server1 or some application on PC11 refers thereto server by name. At Step 1, PC11 sends a DNS message—a DNS query—to the DNS server. At Step 2, the DNS server sends back a DNS reply that lists. Server1’s IP address. At Step 3, PC11 can now send an IP packet to destination address 10.1.2.3, the address used by Server1.
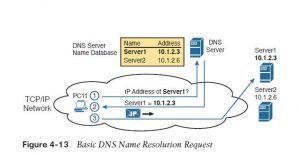
Note that the instance in Figure 4-13 shows a cloud for the TCP/IP network because the details of the network, including routers, don’t matter to the name resolution process. Routers treat the DNS messages a bit like the other IP packet, routing them supported the destination IP address. for instance , at Step 1 within the figure, the DNS query will list the DNS server’s IP address because the destination address, which any routers will use to forward the packet.
Finally, DNS defines much more than just a few messages. DNS defines protocols, also as standards for the text names used throughout the planet , and a worldwide set of distributed DNS servers. The domain names that people use a day when web browsing, which look like www.example.com, follow the DNS naming standards. Also, no single DNS server knows all the names and matching IP addresses, but the information is distributed across many DNS servers. So, the DNS servers of the planet work together, forwarding queries to every other, until the server that knows the answer supplies the specified IP address information.
The Address Resolution Protocol
IP routing logic requires that hosts and routers encapsulate IP packets inside data link layer frames. In fact, Figure 4-11 shows how every router de-encapsulates each IP packet and encapsulates the IP packet inside a new data-link frame. On Ethernet LANs, whenever a host or router must encapsulate an IP packet in a new Ethernet frame, the host or router knows all the important facts to create that header— except for the destination MAC address. The host knows the IP address of the next device, either another host IP address or the default router IP address. A router knows the IP route used for forwarding the IP packet, which lists the next router’s IP address. However, the hosts and routers don’t know those neighboring devices’ MAC addresses beforehand. TCP/IP defines the Address Resolution Protocol (ARP) because the method by which any host or router on a LAN can dynamically learn the MAC address of another IP host or router on the same LAN. ARP defines a protocol that includes the ARP Request, which may be a message that asks the straightforward request “if this is often your IP address, please reply together with your MAC address.” ARP also defines the ARP Reply message, which indeed lists both the first IP address and therefore the matching MAC address.
Figure 4-14 shows an example that uses the same router and host from the bottom a part of the earlier Figure 4-11. The figure shows the ARP Request on the left as a LAN broadcast, so all hosts receive the frame. On the right, at Step 2, host PC2 sends back an ARP Reply, identifying PC2’s MAC address. The text beside each message shows the contents inside the ARP message itself, which lets PC2 learn R3’s IP address and matching MAC address, and R3 learn PC2’s IP address and matching MAC address.
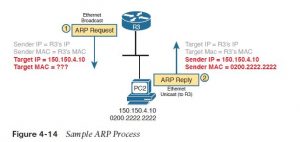
Note that hosts remember the ARP results, keeping the information in their ARP cache or ARP table. a host or router only must use ARP occasionally, to create the ARP cache the primary time. whenever a host or router must send a packet encapsulated in an Ethernet frame, it first checks its ARP cache for the right IP address and matching MAC address. Hosts and routers will let ARP cache entries time out to clean up the table, so occasional ARP Requests are often seen.
ICMP Echo and the ping Command
After you’ve got implemented a TCP/IP internetwork, you would like how to test basic IP connectivity without counting on any applications to be working. the first tool for testing basic network connectivity is that the ping command.
Ping (Packet Internet Groper) uses the web Control Message Protocol (ICMP), sending a message called an ICMP echo request to a different IP address. the pc thereupon IP address should reply with an ICMP echo reply. If that works, you successfully have tested the IP network. In other words, you know that the network can deliver a packet from one host to the other and back. ICMP doesn’t rely on any application, so it really just tests basic IP connectivity—Layers 1, 2, and three of the OSI model. Figure 4-15 outlines the basic process.
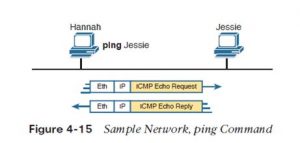
Note that while the ping command uses ICMP, ICMP does much more. ICMP defines many messages that devices can use to help manage and control the IP network. Chapter 20, “DHCP and IP Networking on Hosts,” gives you more information about and examples of ping and ICMP.
Questions related to this topic
- Which network protocol is used to route IP addresses?
- How do routers figure out where a packet needs to go?
- Which applications use TCP protocol?
- Is DNS UDP or TCP?
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com