This article is based on Top 12 Common cybersecurity analyst Interview Questions with Answers as well as job related Introduction.
Introduction
Cybersecurity jobs became one among the foremost in-demand jobs within the IT industry today. With demand, there’s also competition, and to urge employment in Cybersecurity, you would like to be one among the simplest . While having the required Cybersecurity skills is half job done, cracking the interview is another chapter altogether. And to assist you crack the interview, we’ve compiled this list of top Cybersecurity interview questions and answers.
“Skills matter then does Certification!”
Through Live Online cybersecurity training and certifications Learn skills and upgrade yourself. There are lots of courses in cyber security certification, Infosavvy is offering in Mumbai that are CCISO, CEH, CTIA, ECIH, and ECSA .
Top 12 Common Cybersecurity Analyst Interview Questions with Answers
1. How does one define risk, vulnerability and threat on a network?
- Threat: A threat is takes on many various forms. It might be one individual, a technology like malware or maybe natural disasters like earthquakes and floods. Anything that has the potential to cause damage to a computing system like a network, server or a corporation as an entire might be classified as a threat
- Vulnerability: A vulnerability may be a gap within the security of a system that would be employed by cybercriminals or malware (threats) to realize unauthorized entry into a system, like an unpatched server, a weak password or an open port on an unsupervised computer on your network
- Risk: Risk might be seen because the potential for loss or damage when a threat is administered against a vulnerability on your network. this is often the worst-case scenario and is employed as a way to assist motivate for any security-related issues to be detected, prevented or resolved.
2. What does one realize cybersecurity frameworks?
3. what’s a DDoS attack? How is it mitigated?
This is one among the foremost common attacks on the web and is typically wont to take down an internet site . DDoS stands for distributed denial of service. The attack uses an outsized number of clients that flood the affected server with numerous requests that it eventually stops responding to them. This makes actual users that are just sending standard requests to access the web resource unable to attach , thus taking the server offline.
In this scenario, there are a couple of techniques that you simply can use to mitigate a DDoS attack on an internet site . the primary thing that you simply should try is minimize your website’s exposure to potential attacks. this is often done by reducing the amount of ports and resources that are exposed on to the web . Only essential services that expect communications should be internet-facing; everything else should be locked down.
Also Read:- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
4. Why does one need DNS monitoring?
DNS monitoring is just how for you to check connectivity between your local connections and therefore the remainder of the web . DNS monitoring is vital because it gives you a far better idea of the present state of your connections, helping you to troubleshoot issues once they occur. this is often especially helpful from a cybersecurity perspective if you think any malicious activity.
5. what’s the CIA triad?
CIA stands for Confidentiality, Integrity, and Availability. CIA may be a model that’s designed to guide policies for Information Security. it’s one among the foremost popular models employed by organizations.
Confidentiality:-The information should be accessible and readable only to authorized personnel. It shouldn’t be accessible by unauthorized personnel. the knowledge should be strongly encrypted just just in case someone uses hacking to access the info in order that albeit the info is accessed, it’s not readable or understandable.
Integrity:- Making sure the info has not been modified by an unauthorized entity. Integrity ensures that data isn’t corrupted or modified by unauthorized personnel. If a licensed individual/system is trying to switch the info and therefore the modification wasn’t successful, then the info should be reversed back and will not be corrupted.
Availability:- The data should be available to the user whenever the user requires it. Maintaining of Hardware, upgrading regularly, Data Backups and Recovery, Network Bottlenecks should be taken care of.
6. what’s a three-way handshake?
A three-way handshake may be a method utilized in a TCP/IP network to make a connection between a number and a client. It’s called a three-way handshake because it’s a three-step method during which the client and server exchanges packets. The three steps are as follows:
Step1. The client sends a SYN(Synchronize) packet to the server check if the server is up or has open ports
Step2. The server sends SYN-ACK packet to the client if it’s open ports
Step3. The client acknowledges this and sends an ACK(Acknowledgment) packet back to the server
Related Product:- Certified Ethical Hacker | CEH Certification
7. Are you able to explain SSL encryption?
SSL (Secure Socket Layer) allows for safe and personal communications between two computers or other devices over the web . it had been originally created to let participants double-check who they were communicating with, allowing them to verify that the opposite party was indeed who they said they were before proceeding with the conversation.
The real value of SSL that the majority people are conversant in is when it’s used with HTTPS on port 443. this is often seen one among the foremost secure ways of traversing the web , because it allows your communications to be encrypted and made inaccessible to other parties.
SSL has largely been replaced by Transport Layer Security (TLS) lately , albeit the term SSL remains wont to describe TLS. you’ll hear the term TLS/SSL getting used to explain secure HTTPS protocols.
8. What steps will you’re taking to secure a server?
Secure servers use the Secure Sockets Layer (SSL) protocol for encoding and decryption to guard data from unauthorized interception.
Here are four simple ways to secure server:
Step 1: confirm you’ve got a secure password for your root and administrator users
Step 2: subsequent thing you would like to try to to is make new users on your system. These are going to be the users you employ to manage the system
Step 3: Remove remote access from the default root/administrator accounts
Step 4: subsequent step is to configure your firewall rules for remote access
9. What are a number of the common Cyberattacks?
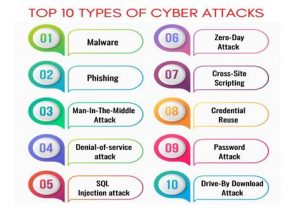
Learn more:- 2020 Top 10 Cyber Attacks in India
10. what’s a Brute Force Attack? How are you able to prevent it?
Brute Force may be a way of checking out the proper credentials by repetitively trying all the permutations and combinations of possible credentials. In most cases, brute force attacks are automated where the tool/software automatically tries to login with an inventory of credentials. There are various ways to stop Brute Force attacks. a number of them are:
- Password Length: you’ll set a minimum length for password. The lengthier the password, the harder it’s to seek out .
- Password Complexity: Including different formats of characters within the password makes brute force attacks harder. Using alpha-numeric passwords along side special characters, and upper and small letter characters increase the password complexity making it difficult to be cracked.
- Limiting Login Attempts: Set a limit on login failures. for instance , you’ll set the limit on login failures as 3. So, when there are 3 consecutive login failures, restrict the user from logging certain a while , or send an Email or OTP to use to log within the next time. Because brute force is an automatic process, limiting login attempts will break the brute force process.
11. What are the various layers of the OSI model?
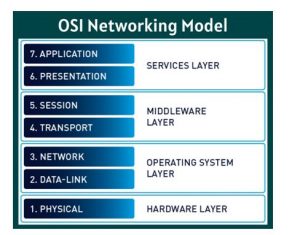
Learn more:- Introduction of OSI Networking Model
12. What are black hat, white hat and gray hat hackers?
Black hat hackers: are known for having vast knowledge about breaking into computer networks. they will write malware which may be wont to gain access to those systems. this sort of hackers misuse their skills to steal information or use the hacked system for malicious purpose.
White hat hackers: use their powers permanently deeds then they’re also called Ethical Hackers. These are mostly hired by companies as a security specialist that attempts to seek out and fix vulnerabilities and security holes within the systems. They use their skills to assist make the safety better.
Grey hat hackers: are an amalgamation of a white hat and black hat hacker. they appear for system vulnerabilities without the owner’s permission. If they find any vulnerabilities, they report it to the owner. Unlike Black hat hackers, they are doing not exploit the vulnerabilities found.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Foot printing Penetration Testing
- Different types of tools with Email Foot printing
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Foot printing tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grapping
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
- Top 5 Firefox extensions for Secure Browsing
- Top 12 Common Cybersecurity Analyst Interview Questions with Answers
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



